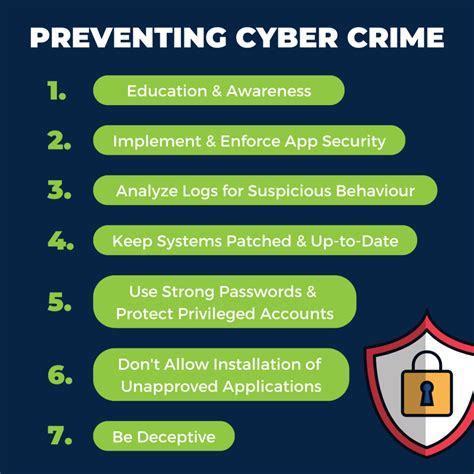
In today's digital age, technology plays a vital role in our daily lives, and its importance cannot be overstated. However, with the rapid advancement of technology, there is a growing concern about tech violations, which can have severe consequences on individuals and organizations. Tech violations can range from cyberbullying and online harassment to data breaches and intellectual property theft. In this article, we will discuss five ways to avoid tech violations and ensure a safe and responsible online experience.
The importance of avoiding tech violations cannot be emphasized enough. Not only can tech violations lead to financial losses, but they can also damage reputations, compromise sensitive information, and even put lives at risk. Furthermore, with the increasing use of technology in various aspects of our lives, the risk of tech violations is higher than ever before. Therefore, it is essential to take proactive measures to avoid tech violations and ensure a safe and secure online environment.
One of the most effective ways to avoid tech violations is to educate yourself about online safety and security. This includes learning about the different types of tech violations, such as phishing, malware, and ransomware, and how to identify and prevent them. Additionally, it is essential to stay up-to-date with the latest technology trends and best practices for online safety.
1. Use Strong Passwords and Enable Two-Factor Authentication

Using strong passwords and enabling two-factor authentication is one of the most effective ways to prevent tech violations. A strong password should be at least 12 characters long and include a combination of uppercase and lowercase letters, numbers, and special characters. Additionally, it is essential to use a unique password for each online account and avoid using easily guessable information such as names, birthdays, or common words.
Two-factor authentication adds an extra layer of security to your online accounts by requiring a verification code sent to your phone or email in addition to your password. This makes it much more difficult for hackers to gain unauthorized access to your accounts.
Benefits of Strong Passwords and Two-Factor Authentication
• Prevents unauthorized access to online accounts • Protects sensitive information from data breaches • Reduces the risk of identity theft and cyberbullying • Ensures compliance with online security regulations
2. Keep Your Software and Operating System Up-to-Date

Keeping your software and operating system up-to-date is essential for preventing tech violations. Outdated software and operating systems can leave your device vulnerable to security risks and make it easier for hackers to gain unauthorized access.
Regular software updates often include security patches and bug fixes that can help prevent tech violations. Additionally, updating your operating system ensures that you have the latest security features and protections.
Benefits of Keeping Your Software and Operating System Up-to-Date
• Protects against security risks and vulnerabilities • Fixes bugs and glitches that can compromise online safety • Ensures compliance with online security regulations • Improves overall device performance and efficiency
3. Be Cautious When Clicking on Links and Downloading Attachments

Being cautious when clicking on links and downloading attachments is crucial for preventing tech violations. Hackers often use phishing emails and malicious links to gain unauthorized access to devices and steal sensitive information.
When receiving emails or messages with links or attachments, it is essential to verify the sender's identity and ensure that the link or attachment is legitimate. Additionally, it is recommended to use antivirus software to scan attachments and links for malware and other security risks.
Benefits of Being Cautious When Clicking on Links and Downloading Attachments
• Prevents malware and ransomware attacks • Protects against phishing and online scams • Ensures online safety and security • Reduces the risk of data breaches and identity theft
4. Use Antivirus Software and Firewalls

Using antivirus software and firewalls is essential for preventing tech violations. Antivirus software can detect and remove malware, including viruses, Trojan horses, and spyware, while firewalls can block unauthorized access to your device and network.
Regularly updating your antivirus software and firewall ensures that you have the latest security features and protections. Additionally, it is recommended to use a reputable antivirus software and firewall to ensure maximum protection.
Benefits of Using Antivirus Software and Firewalls
• Protects against malware and ransomware attacks • Blocks unauthorized access to devices and networks • Ensures online safety and security • Reduces the risk of data breaches and identity theft
5. Monitor Your Online Activity and Report Suspicious Behavior

Monitoring your online activity and reporting suspicious behavior is crucial for preventing tech violations. Regularly monitoring your online activity can help you detect and prevent tech violations, such as data breaches and identity theft.
Reporting suspicious behavior, such as phishing emails or malicious links, can help prevent tech violations and ensure online safety and security. Additionally, it is recommended to use online safety tools, such as browser extensions and plugins, to monitor and report suspicious behavior.
Benefits of Monitoring Your Online Activity and Reporting Suspicious Behavior
• Prevents tech violations and online scams • Ensures online safety and security • Reduces the risk of data breaches and identity theft • Promotes a safe and responsible online environment
In conclusion, avoiding tech violations requires a proactive approach to online safety and security. By educating yourself about online safety and security, using strong passwords and enabling two-factor authentication, keeping your software and operating system up-to-date, being cautious when clicking on links and downloading attachments, using antivirus software and firewalls, and monitoring your online activity and reporting suspicious behavior, you can prevent tech violations and ensure a safe and responsible online experience.
Gallery of Online Safety and Security Tips





What are the most common types of tech violations?
+The most common types of tech violations include data breaches, identity theft, online harassment, and cyberbullying.
How can I protect myself from tech violations?
+To protect yourself from tech violations, use strong passwords and enable two-factor authentication, keep your software and operating system up-to-date, be cautious when clicking on links and downloading attachments, use antivirus software and firewalls, and monitor your online activity and report suspicious behavior.
What are the consequences of tech violations?
+The consequences of tech violations can be severe and include financial losses, damage to reputation, compromise of sensitive information, and even physical harm.